Real CCIE Security Questions Online - 400-251 Practice Questions
To keep pace with real 400-251 CCIE Security Written Exam, new 400-251 practice questions was released on November 30, 2019. It is the latest version for ensuring that you can pass CCIE Security 400-251 exam in the first try. So we highly recommend that if you are preparing for your CCIE Security Certification 400-251 exam, please choose our real CCIE Security questions online for getting Cisco 400-251 practice questions. Real 400-21 CCIE Security questions are verified by Cisco experts who have many years experience in CCIE Security area. 400-251 CCIE Security written exam validates experts who have the knowledge and skills to architect, engineer, implement, troubleshoot, and support the full suite of Cisco security technologies and solutions using the latest industry best practices to secure systems and environments against modern security risks, threats, vulnerabilities, and requirements. With Cisco 400-251 practice questions, you can complete all the exam knowledge points for obvious success.

400-251 CCIE Security Certification Will Be Ended On February 23, 2020
CCIE Security Certification is an expert-level Cisco certification, which is for individuals who have skills to implement and maintain extensive Network Security Solutions using industry best practices. CCIE Security program recognizes security experts who have the knowledge and skills to architect, engineer, implement, troubleshoot, and support the full suite of Cisco security technologies and solutions using the latest industry best practices to secure systems and environments against modern security risks, threats, vulnerabilities, and requirements. There is no prerequisite for CCIE Security certification.
There are two steps to complete CCIE Security certification:
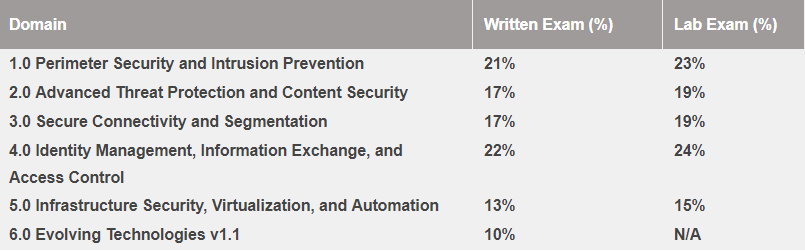
Step One: Pass 400-251 CCIE Security Written Exam
Cisco CCIE Security Written Exam 400-251 utilizes the unified exam topics which includes emerging technologies, such as Cloud, Network Programmability (SDN), and Internet of Things (IoT). It is a two-hour test with 90–110 questions that validate professionals who have the expertise to describe, design, implement, operate, and troubleshoot complex security technologies and solutions. Real CCIE Security Questions Online - 400-251 Practice Questions are collected and verified by our experts who design all the 124 practice questions based on the real Cisco 400-251 exam objectives.
Step Two: CCIE Security Lab Exam
After you complete your CCIE Security Written Exam, you can go on for the lab exam. The eight-hour lab exam tests your ability to get a secure network running in a timed test situation. You must make an initial attempt of the CCIE lab exam within 18-months of passing the CCIE written exam. Candidates who do not pass must reattempt the lab exam within 12 months of their last scored attempt in order for their written exam to remain valid.
We suggest you take your Cisco 400-251 exam before February 23, 2020. Cisco CCIE Security Certification will be ended on February 23, 2020, and also 400-251 exam is not available after February 23, 2020. On February 24, 2020, new Cisco CCIE certification exam will be released. Not only for CCIE Security Certification, most Cisco certifications will be upgraded on February 23, 2020. New programes will be released on February 24, 2020.
Real CCIE Security Questions Online - 400-251 Practice Questions Contain Real Q&As with 100% Passing Guarantee
Now all things you need to do is choosing real 400-251 exam questions to prepare for CCIE Security Written exam well. Real CCIE Security Questions Online - 400-251 Practice Questions contain 124 exam questions and answers, which are all real with 100% passing guarantee. It is recommended to read Cisco 400-251 free exam questions online to check the high-quality of 400-251 exam.
400-251 Free Questions - Real CCIE Security Questions Online
Which criteria does ASA use for packet classification if multiple contexts share an ingress interface MAC address?
A, ASA ingress interface IP address
B. policy-based routing on ASA
D. destination MAC address
E. ASA ingress interface MAC address
G. ASA egress interface IP address
Answer: E
For your enterprise ISE deployment, you want to use certificate-based authentication for all your Windows machines you have already pushed the machine and user certificates out to all the machines using GPO. By default, certificate-based authentication does not check the certificate against Active Directory, or requires credentials from the user. This essentially means that no groups are returned as part of the authentication request.
In which way can the user be authorized based on Active Directory group membership?
A. The certificate must be configured with the appropriate attributes that contain appropriate group formation, which can be used in Authorization policies
B. Configure the Windows supplicant to used saved credentials as well as certificate based authentication
C. Enable Change of Authorization on the deployment to perform double authentication
D. Configure Network Access Device to bypass certificate-based authentication and push configured user credentials as a proxy to ISE
E. Use EAP authorization to retrieve group information from Active directory
F. Use ISE as the Certificate Authority which allows for automatic group retrieval from Active directory to perform the required authorization
Answer: A
In your Corporate environment, you have various Active Directory groups based o the organizational structure and would like to ensure that users are only able to access certain resources depending on which groups(s)they belong to This policy should apply across the network, You have ISE, ASA and WSA deployed, and would like to ensure the propriate policies are present to ensure access is only based on the user s group membership. Addionally, you don't want the user to authenticate multiple times to get access.
Which two ploicies are used to set this up? (choose two)
A. Deploy Cisco TrustSec Infrastructure, with ASA and WSA integrated with the ISE to transparently identity user based on SGT assignment. when the user authenticates to the network. the SGTs can then be used in access
B. Deploy ISE, intergrate it with Active Directory, and based on group membership authirize the user to specific VLANs. These VLANs. These VLANs (with specific subnets) should then be used in access policies on the ASA as well as the WSA
C. Deploy a Single Sign-On Infrastructure such as Ping, and Integrate ISE, ASA and WSA with it. Access policies will be applied based on the users group membership retrieved from the authentication Infrastructure.
D. Configure ISE as an SSO Service Provider, and integrate with ASA and WSA using px Grid. ASA and WSA will be able to extract the relevant identity information from ISE to apply to the access policies once the user has authenticated to the network
E. Integrate ISE, ASA and WSA with Active Directory. Once user is authenticated to the network through ISE, the ASSA and WSA will automatically extract the identity information from ad to apply the appropriate access
F. Configure ISE to relay learned SGTs for the authenticates sessions with the binded destination ad dress using SXP ro SXp speakers that will be used to apply access policies at the traffic ingress point for segmentation
Answer: A, C
All your employees are required to authenticate their devices to the network, be it company owned or employee owned assets, with ISE as the authentication server. The primary identity store used is Microsoft Active directory, with username and password authentication. To ensure the security of your enterprise our security policy dictates that only company owned assets should be able to get access to the enterprise network, while personal assets should have restricted access.
Which option would allow you to enforce this policy using only ISE and Active Directory?
A. Configure an authentication policy that uses the computer credentials in Active Directory to determine whether the device is company owned or personal
B. This would require deployment of a Mobile Device Management (MDM)solution, which can be used to register all devices against the MDM server, and use that to assign appropriate access levels.
Configure an authentication policy that checks against the MAC address database of company assets in ISE end points identity store to determine the level of access depending on the device.
D. Configure an Authorization policy that checks against the mac address database of company assets in ISE endpoint identity store to determine the level of access depending on the device
E. Configure an authorization policy that assigns the device the appropriate profile based on whether the device passes Machine Authentication or no
Answer: E
Which statement about the Sender Base functionality is true?
A. ESA sees a high negative score from Sender Base as very unlikely that sender is sending spam
B. Sender Base uses DNS-based blacklist as one of the sources of information to define reputation score of sender’s IP address.
C. WSA uses Sender Base information to configure URL filtering policies.
D. ESA uses destination address reputation information from SenderBase to configure mail policies
E. Sender Base uses spam complaints as one of the sources of information of define reputation score of receiver IP address
F. ESA sees a high positive score from Sender Base as very likely that sender is sending spam.
G. ESA uses source address reputation to configure URL filtering policies.
Answer: B
You have an ISE deployment with two nodes that are configured as PAN and MnT (Primary and Secondary), and 4 Policy Services Nodes.
How many additional PSNs can you add to this deployment?
A. 0
B. 1
C. 3
D. 5
E. 4
F. 2
Answer: B
What are the advantages of using LDAP over AD is true?
A. LDAP allows for granular policy control, whereas Ad does not
B. LDAP provides for faster authentication
C. LDAP can be configured to use primary and secondary server, whereas AD cannot
D. LDAP does not require ISE to join the ad domain
E. The closest LDAP servers are used for Authentication
Answer: C
In a large organization, with thousands of employees scattered across the globe, it is difficult to provision and onboard new employee devices with the correct profiles and certificates.
With ISE, it is possible to do client provided which four conditions are met. (Choose four)
A. Endpoint operating System should be supported
B. Client provisioning is enabled on ISE
C. The px Grid controller should be enabled on ISE
D. Device MAC Addresses are added to the End point Identity Group
E. Profiling is enabled on ISE
F. SCEP Proxy enabled on ISE
G. Microsoft windows Server is configured with certificate services
H. ISE should be configured as SXP listener to push SGT-To-IP map ping to network access devices
I. Network access devices and ISE should have the PAC provisioning for CTS environment authentication
Answer: A,B,E,F
In an effort to secure your enterprise campus network, any endpoint that connects to the network must authenticate before being granted access. For all corporate-owned endpoints, such as laptops, mobile phones and tables, you would like to enable 802. 1x and once authenticated allow full access to the network. For all employee owned personal devices, you would like to use web authentication, and only allow limited access to the network.
Which two authentication methods can ensure that an employee on a personal device cant use his or her Active Directory credentials to log on to the network by simply reconfiguring their supplicant to use 802.1x and getting unfettered access? (Choose two)
A. Use PEAP-EAP-MSCHAPV2
B. Use EAP-FAST
C. Use EAP-TLS or EAP-TTLS
D. Use EAP-MSCHAPv2
E. Use PAP-CHAP-MSCHAP
Answer: CF
Which statement about SSL policy implementation in a cisco Firepower system is true?
A. Access control policy is optional for the SSL policy implementation
B. If Firepower system cannot decrypt the traffic, it allows the connection
C. Intrusion policy is mandatory to configure the SSL inspection
D. Access control policy is responsible to handle all the encrypted traffic if SSL policy is tried to it
E. Access control policy is invoked first before the SSL policy tied to it
F. If SSL policy is not supported by the system then access control policy handles all the encrypted traffic
Answer: E
A university has hired you as a consultant to advise them on the best method to prevent DHCP starvation attacks in the campus. They have already implemented DH CP snooping and port security to control the situation but those do not fully contain the issue.
Which two actions do you suggest to fix this issue? (Choose two.)
A. Use the ip dhcp snooping limit rate command on Trusted and Untrusted interfaces and set the rate to suitable values that are relevant to each interface respectively.
B. Use the ip dhcp snooping verify mac-address command to ensure that the source MAC address in the DHCP request matches the client hardware address (CHADDR) sent to the DHCP server.
C. Use the ip dhcp snooping verify mac-address command to ensure that the source MAC address in the DHCP request matches the client identifier (CLID) field sent to the DHCP server.
D. Use the ip dhcp snooping limit rate command only to ensure that the source MAC address in the DHCP request matches the client identifier (CLID)field sent to the DHCP server.
E. Use the ip dhcp snooping limit rate command on trusted and untrusted interfaces set to the rate same value
F. Use the ip dhcp snooping limit rate command only on Untrusted interfaces and set the rate to suitable values that are relevant to the interface
Answer: A B
Which statement about Sender Base reputation scoring on an ESA device is true?
A. Application traffic from known bad sites can be throttled or blocked
B. By default, all messages with a score below zero are dropped or throttled
C. Mail with scores in the medium range can be automatically routed for antimalware scanning
D. You can configure a custom score threshold for whitelisting messages
E. A high score indicates that a message is very likely to be spam
F. Sender reputation scores can be assigned to domains, IP addresses, and MAC addresses
Answer: A
Which statement about stealth scan is true?
A. It evades network auditing tools
B. It relies on ICMP "port unreachable" message to determine if the port is open
C. It is used to find the ports that already have an existing vulnerability to exploit
D. It checks the firewall deployment in the path
E. It never opens a full TCP connection
F. It is a directed scan to a known TCP/UDP port
Answer: A
Which function of MSE in the WIPS architecture is true?
A. detects over-the-air traffic network anomalies and attacks
B. scans channels without impacting data-serving radios
C. provides view of security threats
D. performs the correlation of security events
E. channel to connect with ISE to implement CoA
F. applies rogue policy to mitigate rogue threats
G. detects rogue Aps
Answer: D
A sneaky employee using an Android phone on your network has disabled DHCP, enabled its firewall, and modified its Http user-agent header to fool ISE into profiling it as a windows 10 machine connected to the wireless network. this user can now get authorization for unrestricted network access using his Active Directory credentials because your policy states that a windows device using AD credentials should be able to get full network access.
However, an Android device should only get access to the web proxy.
Which two steps can you take to avoid this sort of rogue behavior? Choose two)
A. Modify the authorization policy to allow only Windows machines that have passed machine authentication to get full network access.
B. Create an authentication rule that allows only a session with a specific Http user-agent header
C. Allow only certificate-based authentication from Windows end points, such as EAP-TLS or PEAP-TLS. If the end point uses MSCHAPv2(EAP or PEAP), the user is given only restricted access
D. Chain an authorization policy to the windows authorization policy that performs additional NMAP scans to verify the machine type before access is allowed
E. Add an authorization policy before the windows authorization policy that redirects a user with a static IP to a web portal for authentication
F. Perform CoA to push a restricted access when the machine is acquiring address using DHCP.
Answer: A, C
All above 400-251 free exam questions are parts of real Cisco 400-251 practice questions. From these 400-251 free questions, you can find that Real CCIE Security Questions Online - 400-251 Practice Questions is great for passing Cisco 440-251 CCIE Security Written Exam.
- TOP 50 Exam Questions
-
Exam
All copyrights reserved 2025 PassQuestion NETWORK CO.,LIMITED. All Rights Reserved.

